What is Shadow IT?
Before the cloud, enterprise employees could access only systems or applications made available by IT, which procured and managed packaged software for the organization. Licensing, software updates, and access rights were all controlled by IT. It was the time of “Zero Trust.”
The onset of self-serve made it possible to adopt outside such IT boundaries. They could choose to work with the tools that enabled them to get their jobs done more quickly or efficiently, so the area of unsanctioned IT solutions had begun.
Why employees use Shadow IT
One of the biggest reasons employees engage in Shadow IT is to work more efficiently. For example, an employee may discover a better marketing tool to execute a marketing campaign. Once they begin using it, it could spread to other department members.
Shadow IT is increasing as more and more people use cloud-based applications. This trend is driven by the increasing availability of these applications, which are typically much easier to use than traditional packaged software. Shadow IT also extends to employees' personal devices, such as smartphones and laptops, which they bring with them to work (known as bring your own device, or BYOD).
Shadow IT can pose a risk, so should you embrace it or restrict it?
The bottom line is that if IT isn’t aware of a system or application, they can’t support it or ensure it is secure. However, not all Shadow IT is inherently dangerous, but certain features like file sharing/storage and collaboration can result in sensitive data leaks.
Shadow IT can be beneficial because it can bypass the IT approval process, which can be time-consuming. For many employees, IT approval is a productivity bottleneck, especially when they can get their solution up and running quickly.
Having IT act like an Orwellian “Big Brother” isn’t always conducive to productivity, so distinguishing between good and bad Shadow IT is the better way to allow for innovation and minimize risk. Adopting this middle ground can enable end users to find the best solutions while allowing IT to control data and user permissions for the applications. End users finding their own solutions with IT controlling data and user permissions for applications can help lessen IT's burden by freeing up time to focus on more business-critical tasks.
Top 3 risks related to bad Shadow IT
Bad Shadow IT has risks we need to consider. However, weighing such risks with the possible business benefits of embracing Shadow IT is essential.
Increased risk of data loss
When a system runs outside the IT team’s control, it does not receive the same attention regarding backup and recovery procedures. It is up to the employee or department running the resource to take care of this. Without a proper backup and recovery strategy or the resources to effectively handle these tasks, essential data may be lost if there is an incident. This could have severe ramifications if the data is critical to business.
Increased risk of data breach
Just as IT has no control over backup and recovery with Shadow IT, they have no control over who is accessing the resource. There may be contractors or employees with privileged access that shouldn’t be able to see, modify, or copy specific data. Employees that have resigned or been terminated may still have access. There is no control over who has an account and what those accounts can do.
You also have to consider credential theft as a possibility. With Shadow IT resources operating under the radar, there is no one to monitor access logs to look for anything out of the ordinary that may indicate a breach.
Cyber security risks
Hackers often take advantage of vulnerabilities in the software when they want to access something illegally. The software vendor issues a patch when a vulnerability is known to exist. IT and security teams take the patching of systems seriously. Patches are tested and applied based on the seriousness of the threat they address.
So it is clear that risks need to be addressed, but the answer is not Zero Trust. Instead, the answer is to embrace and manage such risks to promote innovation.
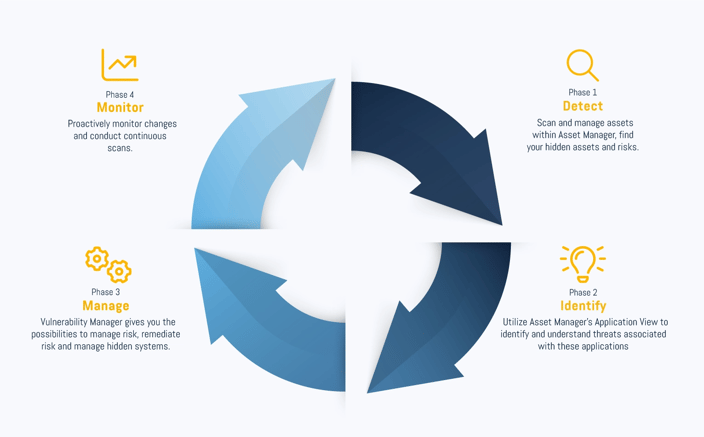
Embrace Shadow IT by adopting Next-Gen Vulnerability Management
To embrace Shadow IT, the IT department needs to discover all the unsanctioned systems or applications running throughout the distributed organization. That's where an automated asset management tool comes into play. An automatic asset discovery and vulnerability assessment tool, like Holm Security's Next-Gen Vulnerability Management Platform (VMP), can help your IT department discover all unsanctioned systems and applications running throughout their organization. The tool will not only identify potential risks to the organization so that IT can take the most appropriate next step but also assist in prioritizing which technical assets are currently the most vulnerable, down to the individual user level.
With the adoption of Next-Gen Vulnerability Management, your organization can embrace Shadow IT rather than adopting restrictive measures like Zero Trust. This will give your employees the freedom to choose the software their department is mainly accustomed to or that provides the most optimal productivity to the organization whilst simultaneously minimizing risks. In other words, with the adoption of Next-Gen Vulnerability Management, gone are the days of restrictive IT measures such as Zero Trust.







