 May 15, 2025 — Vulnerability management
Introducing the next generation of vulnerability remediation
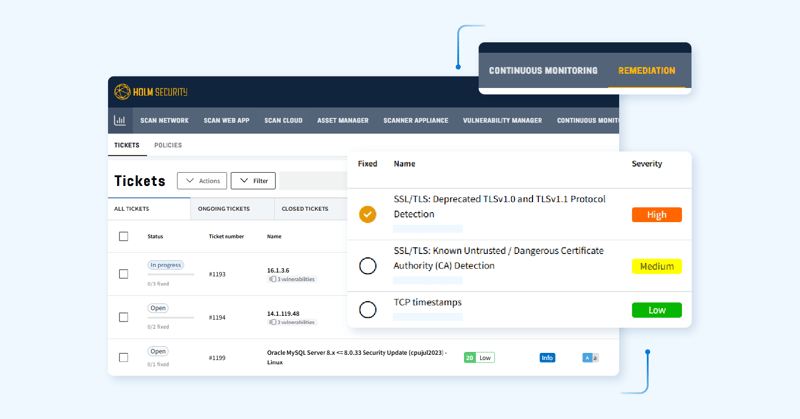
We’re excited to introduce a new generation of vulnerability remediation that's designed to help security teams work smarter, respond faster, and scale with ease.
May 15, 2025 — Vulnerability management
Introducing the next generation of vulnerability remediation
We’re excited to introduce a new generation of vulnerability remediation that's designed to help security teams work smarter, respond faster, and scale with ease.
 May 15, 2025 — Vulnerability management
Introducing the next generation of vulnerability remediation
We’re excited to introduce a new generation of vulnerability remediation that's designed to help security teams work smarter, respond faster, and scale with ease.
May 15, 2025 — Vulnerability management
Introducing the next generation of vulnerability remediation
We’re excited to introduce a new generation of vulnerability remediation that's designed to help security teams work smarter, respond faster, and scale with ease.









