Do I need to care about compliance with industry standards?
Compliance provides a framework for businesses to identify potential cyber security risks, implement controls to mitigate those risks, and establish a plan to respond to incidents. These standards are designed to provide a baseline of security controls that organizations should have to protect their data and systems. Compliance with these standards also demonstrates a commitment to protecting customer information and maintaining the trust of customers.
The consequences of non-compliance
Non-compliance with industry standards can have serious consequences. Cyber security incidents can lead to financial losses, loss of reputation, and in the worst case, even legal action. In fact, the cost of a data breach for an organization can be significant. IBM’s 2022 Cost of a Data Breach report states that organizations with high levels of compliance failures experienced an average cost of US$5.57 million due to cyberattacks. The report further highlights that there was a significant difference of USD 2.26 million, or 50.9%, between organizations with high levels vs. low levels of compliance failures. Essentially, the more an organization enforces compliance standards, the less negative impact a potential breach will have.
Why PCI DSS compliance should be a top priority
PCI DSS compliance is required for any industry that processes, stores, or transmits credit card data. This includes various industries, such as retail, hospitality, healthcare, e-commerce, finance, education, transportation, and more. In short, any organization that accepts credit card payments or handles credit card information must comply with PCI DSS.
So why is it so essential to comply? Below is a list of the key reasons why.
Reducing the risk of data breaches
Non-compliance with PCI DSS standards can lead to data breaches that result in the loss or theft of payment card data. These breaches can be costly, not just in terms of financial losses but also in terms of damage to reputation and loss of customer trust.
Compliance with legal & regulatory requirements
Many industries, including the payment card industry, are subject to legal and regulatory requirements for protecting sensitive data. Compliance with PCI DSS is often required by law and payment card brands like Visa, MasterCard, etc. Failure to comply can result in significant fines and penalties.
Improved security posture
To avoid the devastating consequences of a cyberattack, it is essential not to wait for one to occur before strengthening your security defenses. Instead, take proactive measures to identify potential vulnerabilities and implement security controls to mitigate those risks. This will not only improve your overall security posture but also help you maintain compliance.
Maintaining customer trust
Complying with PCI DSS demonstrates your organization's dedication to protecting sensitive data, which can help build and maintain customer trust. Customers are likelier to choose businesses they trust to safeguard their information, so becoming PCI DSS compliant can increase customer loyalty.
Overall, PCI DSS compliance is essential for cyber security because it helps protect sensitive payment card data, reduces the risk of data breaches, ensures compliance with legal and regulatory requirements, improves security posture, and ultimately maintains customer trust.
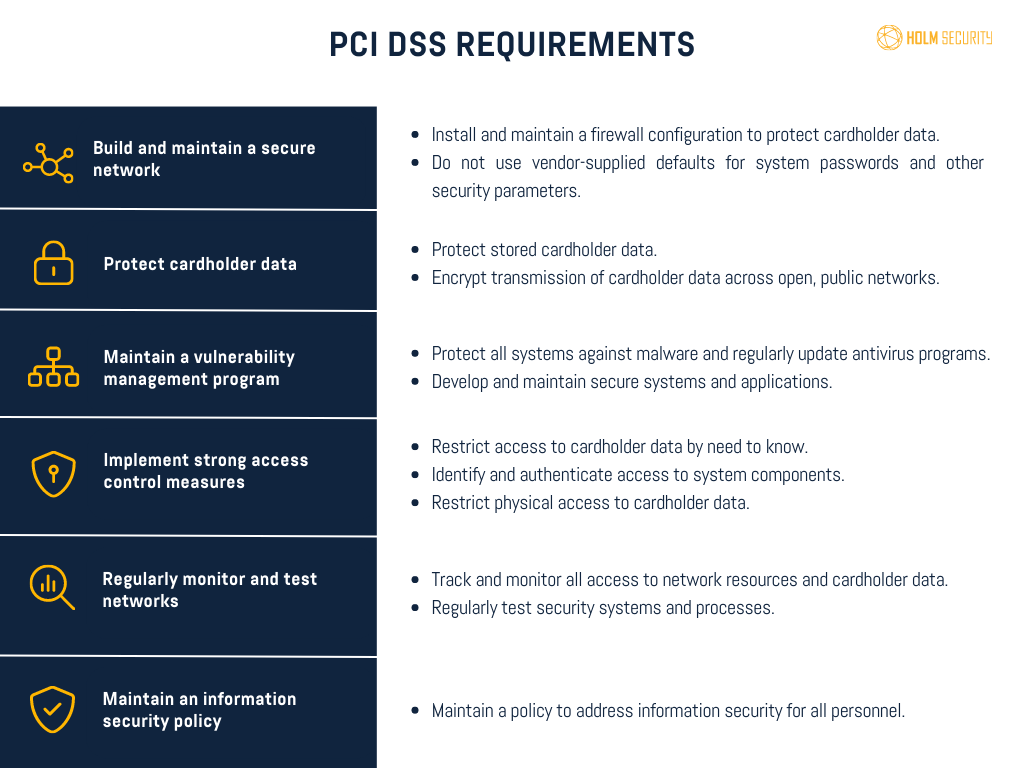
The 12 requirements of PCI DSS
- Install and maintain a secure network: This includes installing and maintaining firewalls to protect cardholder data.
- Protect cardholder data: Cardholder data must be encrypted both when stored and transmitted.
- Maintain a vulnerability management program: Regularly scan for vulnerabilities and patch any security holes in the system.
- Implement strong access control measures: Access to cardholder data should be restricted to authorized personnel only.
- Regularly monitor and test networks: Systems and processes must be regularly monitored to ensure the security controls are functioning properly.
- Maintain an information security policy: An information security policy must be in place, and all personnel must be trained and aware of their responsibilities for ensuring compliance.
- Restrict physical access to cardholder data: Physical access to cardholder data should be restricted and monitored.
- Regularly test security systems and processes: Security systems and processes must be tested regularly to ensure they are effective.
- Maintain a data protection program: Ensure that sensitive data is always protected.
- Monitor and test security controls: Security controls should be monitored and tested continuously to ensure their effectiveness.
- Implement an incident response plan: An incident response plan should be in place to manage security breaches or other incidents.
- Regularly review and update security policies: Security policies should be reviewed and updated regularly to ensure they remain effective in addressing emerging threats and vulnerabilities.
The costly consequences of ignoring PCI DSS standards: Real-life examples
Several high-profile cyber security incidents have occurred over the years due to non-compliance with the PCI DSS industry standard. Here are a few examples:
Target
In 2013, Target experienced a massive data breach in which hackers accessed the personal and financial data of over 70 million customers. The total financial impact of the data breach was estimated to be around $162 million. This included the costs of investigating the breach, enhancing security measures, providing identity theft protection and credit monitoring services to affected customers, and settling numerous lawsuits related to the violation. Additionally, Target experienced a decline in sales due to the negative impact on customer trust and its reputation. Target was found to be non-compliant with the following PCI DSS requirements:
- Inadequate network segmentation: Target's network was inadequately segmented, allowing the cybercriminals to move freely throughout the system and access sensitive data.
- Weak password management: Cybercriminals gained access to Target's network by stealing login credentials from a third-party vendor with weak password management.
- Lack of monitoring: Target failed to adequately monitor its network for suspicious activity, allowing the cybercriminals to remain undetected for an extended period.
- Failure to patch vulnerabilities: Target did not patch a known vulnerability in its payment system software, which the cybercriminals exploited to access customer data.
These failures led to one of the largest data breaches in history and resulted in significant financial losses and damage to Target's reputation.
Home Depot
In 2014, Home Depot suffered a PCI violation that resulted in the compromise of payment card information belonging to around 56 million customers. The violation occurred because the company had not implemented sufficient security measures, such as encryption, to protect customer payment card data. As a result, it cost Home Depot an estimated $179 million. This included the expenses of investigating the breach, enhancing security measures, providing identity theft protection and credit monitoring services to affected customers, and settling numerous lawsuits linked to the violation. Additionally, Home Depot experienced a decline in sales due to the negative impact on customer trust and its reputation.
Adobe
In October 2013, Adobe suffered a significant data breach that compromised login information for around 38 million users, including user IDs, passwords, and credit card data. The breach had substantial financial and legal consequences for Adobe, leading to several class-action lawsuits, settlements, and a drop in the company's stock price. The total financial impact of the breach was estimated to be around $1.1 billion. The breach occurred due to Adobe's failure to comply with PCI DSS security measures, including the encryption of customer data, as mandated by the standard.
So how should I go about getting my company PCI DSS compliant?
One way to ensure PCI DSS compliance is to use a vulnerability management provider. In fact, a vulnerability management provider can be a critical partner in achieving and maintaining PCI DSS compliance.
This provider can perform regular scans and vulnerability assessments to identify and address potential security vulnerabilities within your payment card environment. They can also help you develop and implement policies and procedures that meet the PCI DSS requirements and provide guidance on remediation efforts.
When selecting a provider, choosing one approved by the PCI Security Standards Council (SSC) that has experience working with the PCI DSS standards is essential. The provider should also be able to provide you with a report of their findings and recommendations for improving your PCI DSS compliance.
Learn how Holm Security, an approved PCI DSS complaint Next-Gen Vulnerability Management provider, can help you start your compliance journey today.







