The NIS & NIS2 Directives
The first version of NIS entered into force in 2018. The main purpose of NIS is to create a more resilient and secure digital environment within the EU member states by establishing common cyber security standards, enhancing critical infrastructure protection, promoting risk-based cyber security practices, and fostering cooperation and information-sharing among member states and relevant stakeholders.
The threat landscape is constantly changing, and the threats are getting bigger. The EU has decided to develop a second version of NIS. The NIS2 Directive will take effect throughout 2025 and seeks to enhance the work further started with the NIS Directive.
New in the NIS2 Directive
The NIS2 Directive largely follows the same principles as NIS but with several important additions. NIS2 contains:
- More entities and sectors (industries) covered
- New methods of selection and registration
- New incident notification deadlines
- Greater accountability for management and personal responsibility
- Introduction of sanctions, like those included in GDPR
- Mandatory incident reports, also for so-called “near-misses”

Countdown to NIS2 becoming law: Are you ready?
Download our
NIS2 Reference Guide
Requires a risk-based & systematic approach
Implementing risk-based and systematic cyber security practices is an important component of NIS and NIS2. Organizations should assess and manage cyber security risks effectively based on their specific circumstances and the potential impact of cyber incidents. A systematic approach goes hand in hand with creating a proactive approach – a pillar in any cyber security strategy.
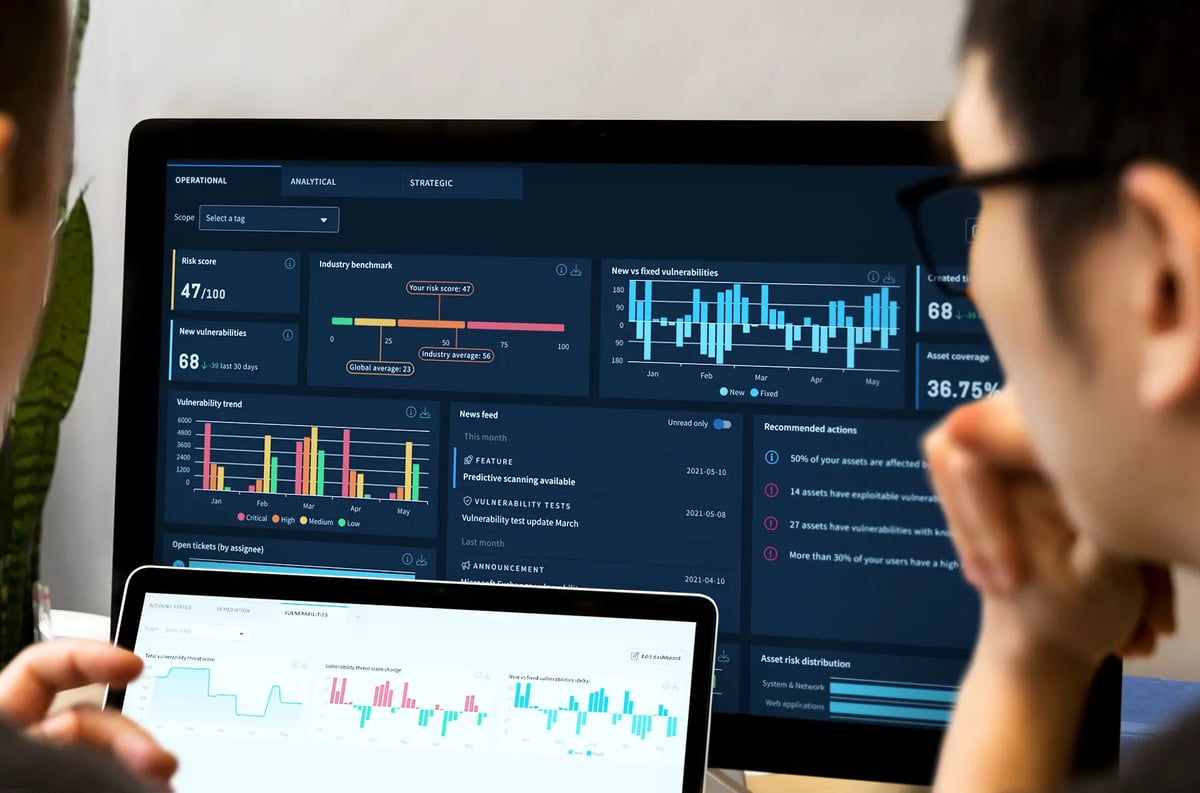

Cyber security risk management measures
Essential and important entities must take appropriate and proportional technical, operational, and organizational measures to manage the risks posed to the systems that underpin their services and prevent or minimize the impact of incidents on their and other services.
Such measures include:
- Risk analysis and information system security
- Incident handling
- Business continuity measures (back-ups, disaster recovery, crisis management)
- Supply chain security
- Security in system acquisition, development, and maintenance, including vulnerability handling and disclosure
- Policies and procedures to assess the effectiveness of cyber security risk management measures
- Basic computer hygiene and training
- Policies on appropriate use of cryptography and encryption
- Human resources security, access control policies, and asset management
- Use of multi-factor secured voice/video/text communication & secured emergency communication
Management responsibilities under NIS2
Management accountability is yet another cornerstone of NIS2, as the new Directive will obligate management to take ownership of their organizations’ cyber security maturity level. This will include conducting risk assessments and approving risk treatment plans, meaning management must partake in cyber security training. The Directive also mandates organizations train their employees on cyber security risk and response.
Failure by management to comply with NIS2 requirements could result in serious consequences, including liability, temporary bans, and administrative fines as provided for in the implementing national legislation.
Management bodies of essential and important entities must:
- Approve the adequacy of the cyber security risk management measures taken by the entity
- Supervise the implementation of risk management measures
- Follow training to gain sufficient knowledge and skills to identify risks and assess cyber security risk management practices and their impact on the services provided by the entity
- Offer similar training to their employees on a regular basis
- Be accountable for non-compliance

RECORDED WEBINAR
Upgrade your cyber defense to comply with NIS2
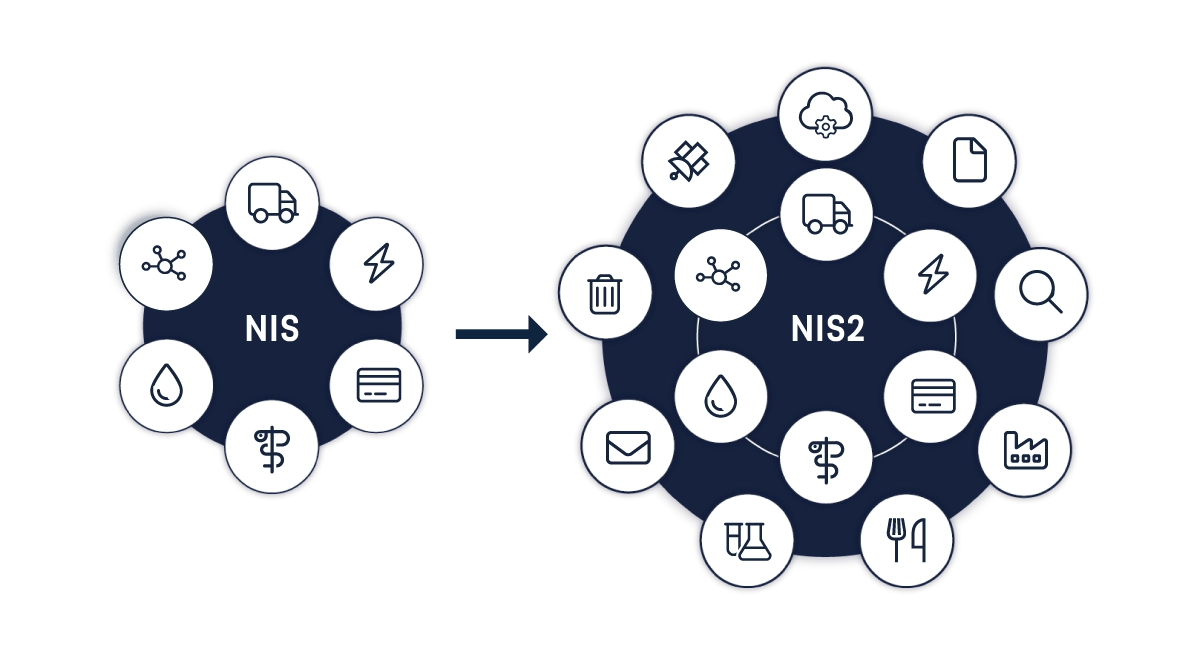
Industries impacted by NIS2
The first version of NIS impacted a limited number of sectors. With NIS2 comes extended coverage to a total of 15 industries. The former distinction between Operators of Essential Services (OES) and Digital Service Providers (DSPs) in the original NIS Directive is replaced by a distinction between Essential Entities (EE) and Important Entities (IE), depending on factors such as size, sector, and criticality to society. Both entity types must follow the NIS2 framework for cyber security, whereas essential entities have stricter reporting and supervision requirements.
Essential entities
Energy
Including subsectors electricity, oil, and gas.
Transportation
Including subsectors of air transport, rail transport, shipping, and road transport.
Health
Including subsector healthcare environments (including hospitals and private clinics).
Public administration
Banking & financial market infrastructure
Banks and financial market infrastructure, e.g. payment services.
Digital infrastructure
Digital infrastructure such as the delivery of DNS and TLD registries.
Water supply
Space
Important entities
Digital providers
Food
NIS2 categorizes the food sector as an important entity. Encompassing all stages from farming to food processing, packaging, transportation, and retail sales.
Chemicals
Manufacturing
Research
Waste management
Postal & courier services
Holm Security helps you take a major leap towards NIS/NIS2 compliance
Holm Security helps hundreds of organizations throughout the EU to comply with the NIS Directive and is now helping more to comply with NIS2. We provide the tools you need to take huge steps towards compliance.
These tools allow you to:
- Perform automated and continuous (systematic) risk assessments
- Create a proactive approach towards cyber security
- Implement basic cyber hygiene practices and cyber security training
- Provide the tools needed to secure the supply chain
- Help management supervise the implementation of risk management
- Demonstrate compliance based on data and reports
Frequently asked questions
We have the answers to your questions about NIS and NIS2. Read more in our FAQ.
FAQs
We'll help you comply with the NIS2 Directive.
Get started today.
Getting you ready for NIS2 compliance

What is NIS2 & how will it affect your organization?
Under the NIS2 Directive, more entities and sectors will be required to take steps that will aid in improving cyber security in Europe. In addition to addressing supply chain security, NIS2 streamlines reporting obligations introduces stricter supervisory measures, and introduces more enforcement requirements.

How the NIS2 cyber security Directive will impact you
As part of this webinar, we will be joined by Anders Jonson, a cyber security expert and Senior Advisor at ENISA, who has been involved in the development of NIS2 for the EU.

NIS2 Reference Guide: Securing critical infrastructure
Our NIS2 Reference Guide is packed with essential insights and lays out actionable steps for organizations to take for compliance.

