Secure Your Digital Backbone with Next-Gen Vulnerability Management
Digital infrastructure is the backbone of our interconnected world. However, with its growth and evolution comes vulnerabilities. These weaknesses are opportunities for malicious actors to jeopardize operations, leak data, and threaten businesses. Stop business-critical failures before they happen with our Next-Gen Vulnerability Management platform, tailored to your needs.
Addressing Cybersecurity Challenges in The Digital Infrastructure Sector
Ransomware Attacks
Ransomware can freeze your operations and slap a hefty price tag on the key. With proactive vulnerability management, you can spot and secure weak points, keeping cyber threats outside where they belong.
IoT Security
IoT devices multiply your digital entry points, making you more exposed to potential breaches. Vulnerability management systematically identifies, assesses, and rectifies these weak spots. Elevate your defense with vulnerability management.
Compliance
Stringent regulations like NIS2 and GDPR undeniably escalate cyber security challenges in the digital infrastructure domain, adding layers of complexity and cost. Streamline compliance processes, and reduce overheads while mitigating risk with our platform.
Third-Party Vendor Security
With each vendor requiring access, the potential for unwanted guests increases. Constantly scan and secure entry points to prevent unwanted guests with our platform. We'll help safeguard your assets and manage third-party risks effectively.


Get Ready for NIS2
In 2024, NIS2 will set a new cybersecurity benchmark for the digital infrastructure sector across the EU. Well help you enhance your standing, secure customer trust, and ensure compliance.
-
Unleash the Power of Risk Assessment
Prioritize security gaps and address new risks continuously to stay ahead of cyber threats. Our platform offers incident reporting for incidents and vulnerabilities, allowing you to monitor your security and proactively identify trends. -
Ensure Business Continuity
Our platform enables you to easily identify vulnerabilities, minimize risk, and maintain compliance with just a few clicks. With our help, you can navigate the complexities of NIS compliance with ease, leaving you free to focus on what really matters - growing your business.

GDPR Compliance Made Simple
With Holm Security, you can get a comprehensive assessment of vulnerabilities across your entire attack surface. Our solution can help your security team to efficiently reduce risks. Identify and safeguard systems that store and use sensitive data, preventing GDPR fines.
-
Prioritize Systems Handling Personal Data
Tag specific systems that process personal data as more important than other systems, amplifying the risk score of the asset and ensuring that the vulnerabilities found on these assets are prioritized for remediation. -
Keep Tabs on the Remediation Progress
Integrate with ticketing solutions like JIRA and ServiceNow to seamlessly fold remediation into your IT team’s existing workflow and ensure SLAs are met, and GDPR systems are patched in a timely manner.

Start Your NIS2 Compliance Journey
Try Our Platform for Free Today!
Empower Your Security Team
& Maximize Efforts
Holm Security delivers the broadest coverage and most thorough assessment of vulnerabilities across your entire attack surface. By leveraging our solution, your security resources can make a greater impact on risk reduction with minimal effort.
-
See Your Entire Attack Surface
Gain precise comprehension of all assets and vulnerabilities across your entire attack surface. This includes dynamic components such as data centers, network switches, and virtual machines that form the backbone of your digital infrastructure. With increased visibility, you can prioritize mitigation efforts and guarantee comprehensive protection. -
Transform Your Organization's Cyber Defense
Don't waste your time on vulnerabilities that don't pose a real threat. Our Unified Vulnerabilities view lets you track all risks in one place, including network, web, device, and phishing recipients. The new threat score prioritizes vulnerabilities for technical and human assets, making risk management easier.
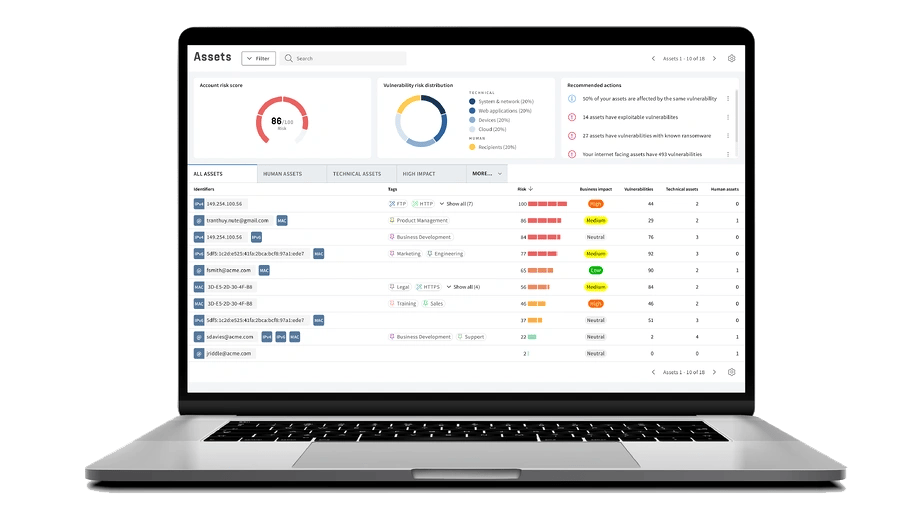
Get A Complete Picture of Your Cyber Security Defense
Detect
Scan every potential entry point for attackers. Efficiently monitor and manage all of your systems, applications, endpoints, and employees.
Assess
Up your security game with fast and accurate scans, and prioritize the vulnerabilities that truly put you at risk from the ones that don’t.
Remediate
Cut down on unnecessary headaches with straightforward risk in real-time right from your dashboard. Measure and communicate progress effectively.
See For Yourself
Try Our Platform for Free Today!
Why Choose Our Vulnerability Management Solution?
Tailored Defense
Our solution is designed to tackle the security challenges inherent in your industry, providing a robust shield against both current and emerging threats.
Operate Without Hiccups
Seamlessly integrate our solution into your current setup. Experience robust protection that ensures your business operations continue without a hitch.
Comprehensive Threat Detection
Our platform offers full visibility across your attack surface and unmatched insights into all assets, including technical and human. Reduce business risks with minimal effort.
See the Difference a Next-Gen Vulnerability Management Platform Makes
From local government to industry-leading retailers, discover how Holm Security helps solve cyber security problems.
Latest news

DORA decoded: Fusing operational resilience & vulnerability management
In this blog post, we're diving deep into DORA - why it's vital for digital service providers and financial institutions and why you should care about it.

Upgrade your cyber defense to comply with NIS2 - A step-by-step guide on how to prepare
This webinar will focus on the practical steps that IT departments need to take to improve their cyber security posture and adhere to NIS2 regulations.



