Secure Your APIs.
Protect Your Business-Critical Data.
Elevate your API security effortlessly. Identify and resolve vulnerabilities, ensuring no potential entry points are left unscanned or exposed to attacks. Safeguard your externally facing applications confidently.
Scan Every Corner of Every Exposed App
Transform Threats into Priorities
Our platform finds and categorizes your high-risk vulnerabilities automatically, converting them from potential threats into top priorities for your team.
Your Schedule
Your Scans
Set your own schedule for continuous scans and let the platform handle the rest, giving you more time for strategic planning.
Scans for OWASP Top 10 API Vulnerabilities
Find vulnerabilities with tailored security scans, such as security misconfigurations and injection flaws, from the OWASP Top 10 API security list.
Cover Multiple Attack Vectors Simultaneously
Identify gaps in your cyber security defense across your entire attack surface. View your vulnerabilities from the organizational level right down to a singular API.
Your Shield Against API Threats
You don’t have time to stay on top of the world’s newest vulnerabilities. With Holm Security, you don’t have to alone. Effortlessly fortify the security of your APIs, guaranteeing equally robust protection as offered to web applications and websites. With Holm Security, you can:
- Conduct thorough scans of your REST, GraphQL, and SOAP endpoints to identify and resolve any security flaws. Quickly assess the security of your APIs.
- Keep entry points for attacks secure and ensure your APIs are always up-to-date.
- Attacks can happen at any time. But that doesn’t mean you have to live in fear. Automate scans – so you can be confident you’ll catch new vulnerabilities quickly.
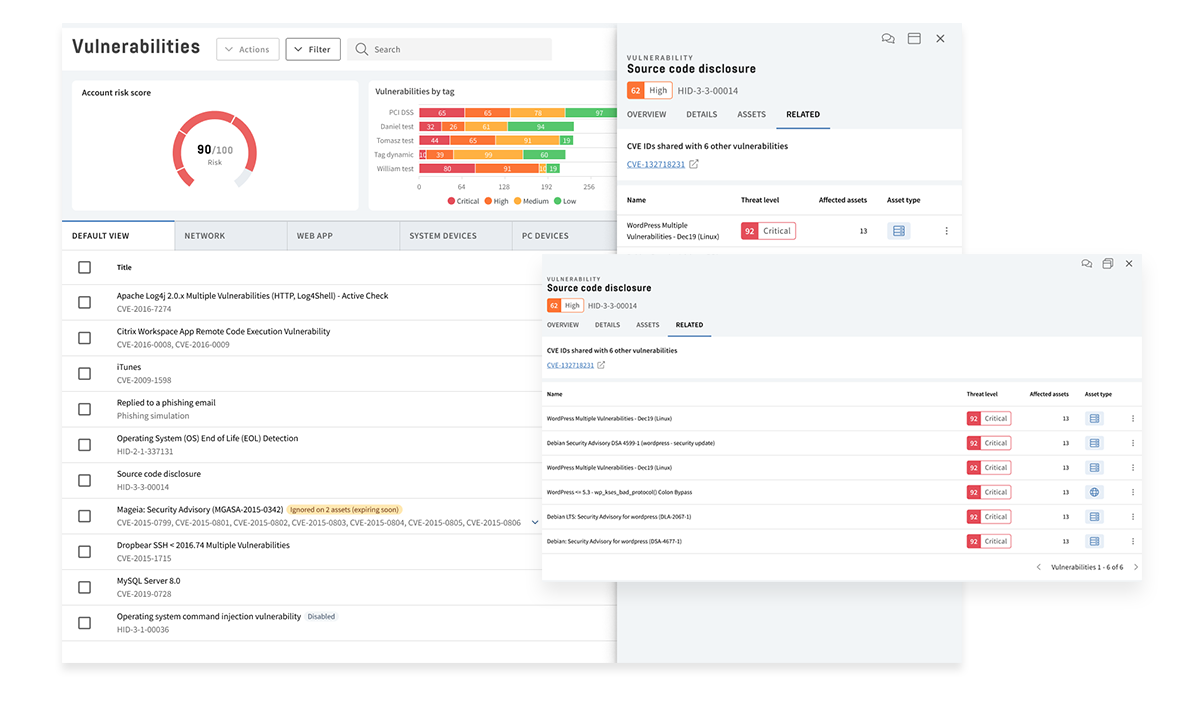
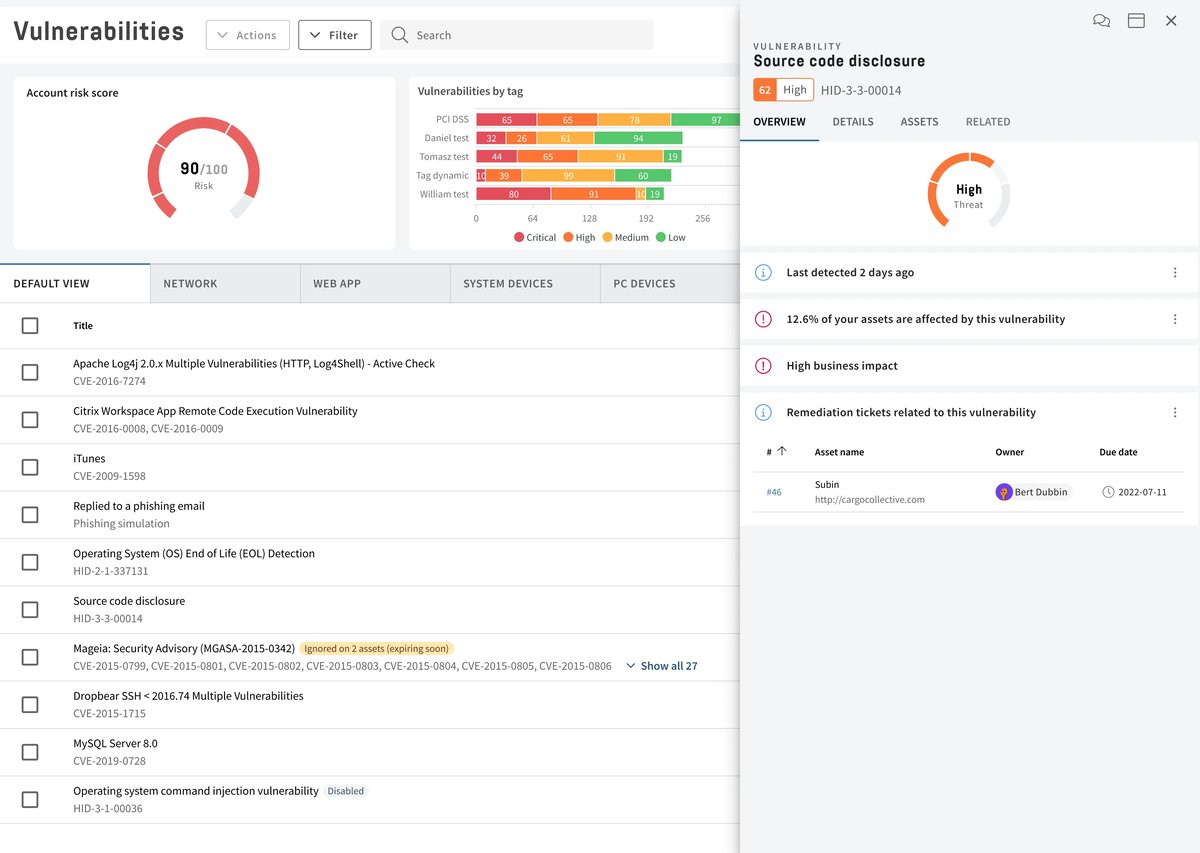
Complete Coverage Through Detailed Scanning
- Get complete visibility of your API endpoints, including coverage for REST APIs, SOAP APIs, and GraphQL API.
- Find vulnerabilities with tailored security scans, such as security misconfigurations and injection flaws, from the OWASP Top 10 API security list.
- Perform scans that provide a 360-degree view of your API security, inside and out. Never miss a beat with our all-encompassing scans.
Incorporate into Your Tech Stack for Effortless Collaboration
- Work in Harmony with Your Team
Effortlessly integrate with your tech stack, including popular platforms like Slack, Jira, Github, and more. Because teamwork really does make the dream work. - Showcase Your Security Prowess with Detailed Reports
Impress your stakeholders and/or customers with comprehensive reports demonstrating your commitment to security; Because seeing truly is believing.
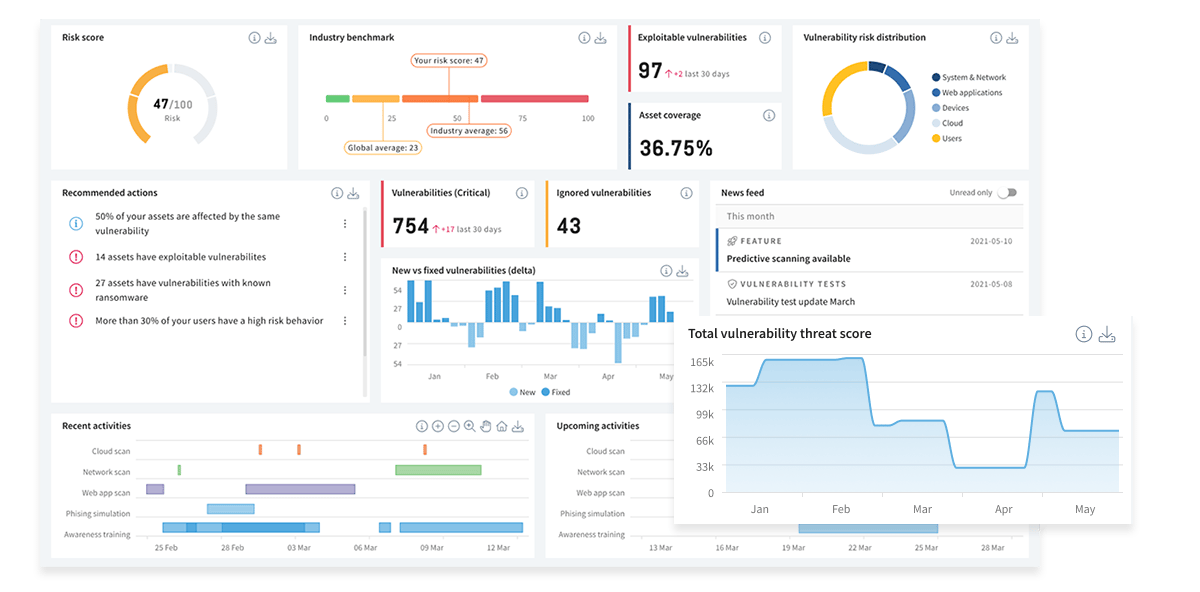
Get A Complete Picture of Your API Security
Detect
Assess
Up your security game with fast and accurate scans,separate the vulnerabilities that truly put you at risk from the ones that don’t.
Remediate
Cut down on unnecessary headaches by minimizing false positives and giving developers all the necessary information to tackle each issue. Keep tabs on everything from start to finish.
TRY IT OUT YOURSELF
Get Ready To Accelerate Your Cyber Security Defense
Latest News

DORA Decoded: Fusing Operational Resilience & Vulnerability Management
In this blog post, we're diving deep into DORA - why it's vital for digital service providers and financial institutions and why you should care about it.

Upgrade Your Cyber Defense To Comply With NIS2 - A Step-by-Step Guide On How To Prepare
This webinar will focus on the practical steps that IT departments need to take to improve their cybersecurity posture and adhere with NIS2 regulations.
See the Difference a Next-Gen Vulnerability Management Platform Makes
From local government to industry-leading retailers, discover how Holm Security helps solve cyber security problems.
Frequently Asked Questions
What Is API Security?
API security refers to the practices, measures, and technologies implemented to protect Application Programming Interfaces (APIs) from unauthorized access, data breaches, and other cyber threats. APIs are sets of rules and protocols that allow different software applications to communicate and interact with each other.
API security is crucial because APIs often serve as gateways to valuable data and functionalities within an organization's systems. By compromising an API, attackers can gain unauthorized access to sensitive information, manipulate data, disrupt services, or launch other malicious activities. Therefore, protecting APIs and ensuring their security is vital for maintaining the overall security posture of an application or system.
What Is an API Endpoint?
In simpler terms, an API endpoint is a specific URL to which a client application can send requests to perform certain actions or retrieve specific information from the API. Each endpoint typically represents a distinct operation or resource within the API.
API endpoints are designed following a specific pattern and adhere to the API's defined structure and conventions. They are typically constructed using the HTTP methods (such as GET, POST, PUT, and DELETE) combined with a specific URL path corresponding to a particular resource or action.
How Does the REST API Security Work?
REST API scanning is a feature of our web application service that enables the detection of vulnerabilities in JSON REST APIs. The process involves injecting vulnerability detection patterns into the APIs to identify various vulnerability classes, including SQL injections, XXE, and deserialization issues.
To initiate the scanning process, you need to provide an OpenAPI specification document. This document is parsed by our scanner and serves as the starting point for identifying vulnerabilities in the REST APIs.
Please note that the OpenAPI specification must be published before Holm Security can perform the API scan. This ensures that our scanning system can access and analyze the API effectively.
Additionally, if you have the API specification in a different file format like WADL, we provide the option to convert it to the required OpenAPI format for seamless scanning.
How Do I Best Secure APIs?
Understanding the locations of your APIs and comprehending the potential exploitation avenues for attackers has become increasingly critical. The significance of regular API scanning cannot be overstated, as it serves as a proactive measure to secure your application ecosystem. By conducting systematic API scans, you can identify vulnerabilities and weaknesses before they can be exploited, enabling you to promptly address and rectify them.


