Build your human firewall with Phishing Simulation & Awareness Training
Strengthen your user defenses to safeguard your organization against phishing and ransomware attacks.
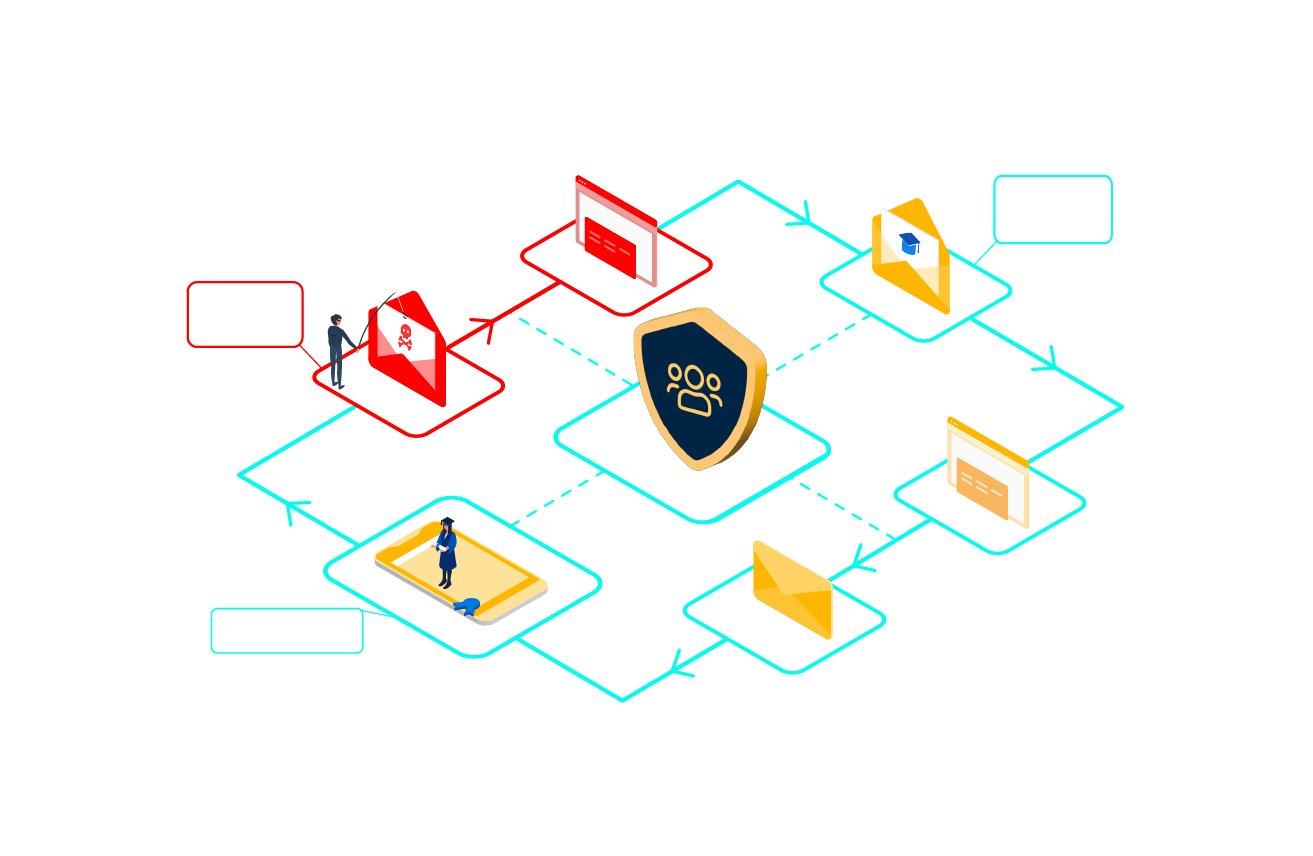
Phishing Simulation & Awareness Training
Phish your users
Expose your users to risk-free phishing simulations based on various email attack templates, such as phishing, spear phishing, and whaling (CFO/CTO fraud).
Automated awareness training
Based on phishing simulation behavior, users receive personalized awareness training in a nano-learning format, featuring best-in-class video content and knowledge verification quizzes. Their training performance is tracked and directly contributes to their individual risk score.
Measure risk & understand trends
Results provide detailed statistics to assess overall risk levels across user groups and individual users. With our unique user risk-scoring system, you can track the development of user resilience over time, gaining insights into progress and areas for improvement.
Risk score based on behavior & vulnerabilities
By combining both phishing simulation and awareness training with computer vulnerability assessments, each user offers a unique opportunity to understand risk holistically taking into account both user behavior and system vulnerabilities.
Build your own
human firewall
Automated workflow
Phishing simulation
Phishing simulation based on ready-made email and web templates.
Tailored awareness training
Automated and tailored awareness training based on ready-made templates.
Knowledge verification quizzes
Follow-up quizzes to verify the user's knowledge and resilience.
Measure risk & trends
Understand current risks and trends over time. Combine user risk behavior and computer vulnerabilities.
Repeat, repeat & repeat
Repeat to keep your users resilient today and in the future.
Understand user risk behavior & computer vulnerabilities
Ready-made best-in-class content
Ready-made phishing templates
Choose from our extensive library of ready-to-use templates, featuring scenarios based on both classic and current threats.
Out-of-the-box awareness training
Out-of-the-box multi-language templates for awareness training and knowledge verification quizzes.
Best-in-class videos
Video content for awareness training based on short and modern videos in your local language.
Modern nano-learning concept
The awareness training programs are based on nano-learning, where training is focused on small, bite-sized pieces of information. This makes it easier to absorb and retain information.
All features and capabilities in Phishing Simulation & Awareness Training

Cyber hygiene a more common compliance requirement
NIS2
Under NIS2, cyber hygiene practices are embedded as fundamental security requirements to build resilience, prevent incidents, and enhance incident response across critical sectors.
PCI DSS
In PCI DSS version 4.0, cyber hygiene practices are foundational to maintaining secure payment environments. The standard emphasizes employee awareness to safeguard cardholder data and support resilient, hygienic security practices.
ISO 27001
In ISO 27001, cyber hygiene practices are foundational elements embedded in policies, procedures, and controls to support information security.
How can we help you?
Your trusted partner

FAQ
What is a phishing simulation?
Phishing simulations are fake phishing attacks that are used as training tools to educate users about how to identify and prevent real phishing attacks.
These simulations typically involve sending simulated phishing emails to a group of users and tracking how many of them fall for the fake attack by clicking on a link or entering their login credentials.
What is the goal of phishing simulation and awareness training?
The goal of phishing simulations is to help users become more aware of the types of phishing attacks that they may encounter, as well as to teach them the strategies and tactics that they can use to protect themselves. This can include things like looking for clues that an email is fake, such as a suspicious sender address or poor grammar, as well as being cautious about clicking on links or downloading attachments from unknown sources.
Are ready-made simulation templates and awareness training programs included?
Yes, all templates can be used out of the box.
What types of phishing simulation templates are available?
We provide a wide range of templates based on current real-world phishing templates, such as:
- Emil phishing
- Spear phishing
- Whaling (CFO/CTO fraud)
Can I create my own phishing templates?
Yes, you can create custom templates based on existing or from scratch.
Can I use my own awareness training content?
Yes, you can integrate it with your awareness content outside Holm Security’s platform.
How do the awareness videos look?
How frequently should I do phishing simulations?
Simulations should be carried out regularly to ensure your users are updated with the latest threats and keep their resilience high. We recommend performing at least 3 to 4 simulations per year.
Does phishing simulation and awareness training require any software?
No software is required. The optional usage of the lightweight endpoint software agent for Windows combines user behavior with computer vulnerabilities.

