Guarding the Grid & Powering Cyber Resilience with Next-Gen Vulnerability Management
Energy companies are at a critical juncture, facing formidable cyber threats that target Operational Technology (OT) and broader societal security infrastructure. The sheer scale of these challenges demands more than just defense—it requires foresight, innovation, and agility. Fortify your energy operations against these looming cyber shadows with our Next-Gen Vulnerability Management platform, meticulously crafted for your unique demands.
Protect Your OT from Cyber Threats
Ransomware
Phishing
Supply Chain Attacks
Foreign Powers


Fueling a Secure Energy Future with NIS2
As we transition to a more sustainable energy landscape in 2024, the NIS2 directive will reshape the cyber security terrain for energy-sector organizations across the EU. Adhering to these rigorous cyber security measures is not just about compliance. For forward-thinking energy firms, it's an opportunity to bolster trust, amplify your brand's reputation, and drive business growth.
-
Unleash the Power of Risk Assessment
The energy sector faces unique and evolving cyber threats. Stay a step ahead by continuously pinpointing security gaps and addressing emergent risks. Our platform provides detailed incident reporting for both vulnerabilities and breaches, offering you a comprehensive overview of your security posture. This enables proactive action, safeguarding your energy assets.
-
Ensure Business Continuity
In the intricate web of energy operations and NIS compliance, our platform stands as your beacon. Swiftly detect vulnerabilities, curtail risks, and ensure you're in line with regulations—all within a user-friendly interface. Let our platform manage the intricacies of NIS2 so you can concentrate on your core mission: illuminating the future with sustainable energy solutions.

GDPR Compliance Made Simple
With the evolving energy landscape, safeguarding personal data becomes even more critical. With Holm Security, we cater specifically to the energy sector's needs, offering a robust assessment of vulnerabilities across all touchpoints. Our solutions ensure your security measures are not only compliant but also efficient, protecting vital data and mitigating GDPR-related penalties.
-
Prioritize Systems Handling Personal Data
Some systems are more crucial than others. Highlight and tag systems involved in processing personal data, emphasizing their significance. By amplifying the risk score of these assets, we ensure that vulnerabilities tied to them are swiftly addressed and remedied. -
Keep Tabs on the Remediation Progress
Integrate with ticketing solutions like JIRA and ServiceNow to seamlessly fold remediation into your IT team’s existing workflow and ensure SLAs are met and GDPR systems are patched in a timely manner.

See For Yourself
Try Our Platform for Free Today!
Empower Your Security Team
& Maximize Efforts
Holm Security delivers the broadest coverage and most thorough assessment of vulnerabilities across your entire attack surface. By leveraging our solution, your security resources can make a greater impact on risk reduction with minimal effort.
-
See Your Entire Attack Surface
Gain precise comprehension of all assets and vulnerabilities across your entire attack surface. This includes dynamic assets related to your energy infrastructure, including communication networks, grid management software, or other industrial control systems. With increased visibility, you can prioritize mitigation efforts and guarantee comprehensive protection. -
Transform Your Organization's Cyber Defense
Don't waste your time on vulnerabilities that don't pose a real threat. Our Unified Vulnerabilities view lets you track all risks in one place, including network, web, device, and phishing recipients. The new threat score prioritizes vulnerabilities for technical and human assets, making risk management easier.
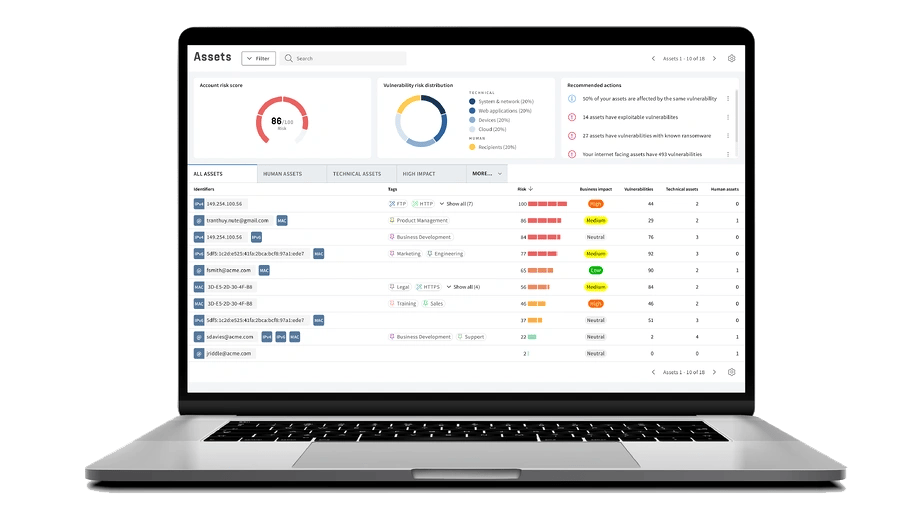
Get A Complete Picture of Your Cyber Security Defense
Detect
Scan every potential entry point for attackers. Efficiently monitor and manage all of your systems, applications, endpoints, and employees.
Assess
Up your security game with fast and accurate scans, and prioritize the vulnerabilities that truly put you at risk from the ones that don’t.
Remediate
Cut down on unnecessary headaches with straightforward risk in real-time right from your dashboard. Measure and communicate progress effectively.
See For Yourself
Try Our Platform for Free Today!
Why Choose Our Vulnerability Management Solution?
Industry Expertise
We specialize in serving the energy sector understanding the specific challenges and risks you face. Our solution is designed to tackle the vulnerabilities inherent in your industry.
Minimal Disruption with Maximum Protection
Our solution is implemented seamlessly into your existing infrastructure, providing robust protection without interrupting your production processes.
Comprehensive Threat Detection
Our comprehensive platform provides exceptional visibility and insight, encompassing all assets, technical and human. Maximize your efforts and reduce business-critical risks with the least amount of effort.
See the Difference a Next-Gen Vulnerability Management Platform Makes
From local government to industry-leading retailers, discover how Holm Security helps solve cyber security problems.

Holm Security VMP provides a holistic overview of vulnerability information in our infrastructure. It scans the entire infrastructure and gives consolidated reports on all loopholes so that we can patch those easily. It is a very user-friendly platform loaded with advanced technical features.
Vinod Sharma
General Manager IT - Hero Future Energies
Holm Security has helped us a lot with our challenges. We now know what is running within our terminals and their security status, providing a starting point for optimizing our IT even further. It strikes me positively how human-centric Holm Security is. I’m not just waived off with an email or ticket.
Patrick Mast
IT Director - Alkion TerminalsLatest news

DORA decoded: Fusing operational resilience & vulnerability management
In this blog post, we're diving deep into DORA - why it's vital for digital service providers and financial institutions and why you should care about it.

Upgrade your cyber defense to comply with NIS2 - A step-by-step guide on how to prepare
This webinar will focus on the practical steps that IT departments need to take to improve their cyber security posture and adhere to NIS2 regulations.



