Secure your cloud-native platforms - today & tomorrow
Identify and remediate vulnerabilities across your cloud-native platforms with Cloud Security Posture Management (CSPM).
A complete solution to protect cloud-native platforms
Multi-cloud platform support
A single pane of glass for all your cloud-native platforms' security posture management.
Find vulnerabilities
Gain complete visibility and actionable context on your most critical misconfigurations so your teams can proactively and continuously improve your cloud security posture.
Increased visibility
Automatically discover and monitor your cloud assets. Streamline the detection and prioritization of critical security risks throughout your cloud.
Agentless deployment
Ensure complete coverage with an API-based, agentless approach without the need for any hardware or software.
Reduce costs
A collection of plugins alerts you to unused resources and misconfigurations that increase your account costs.

Assessment capabilities
Data access misconfigurations
Detect data access misconfigurations, such as public storage buckets or unsecured databases.
Improper network configurations
Identify improper network configurations, such as open ports and overly permissive firewall rules.
Permission misconfigurations
Identify misconfigured Identity and Access Management (IAM) roles, such as excessive privileges or unused accounts, ensuring secure access controls.
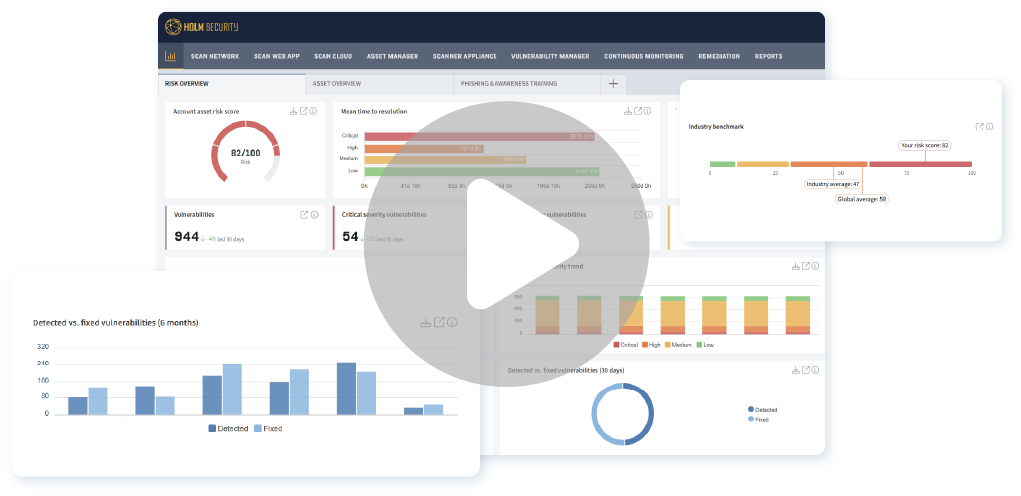
Watch our platform demo
Our market-leading platform is the cornerstone of a proactive cyber defense, empowering you to always stay one step ahead of cybercriminals.
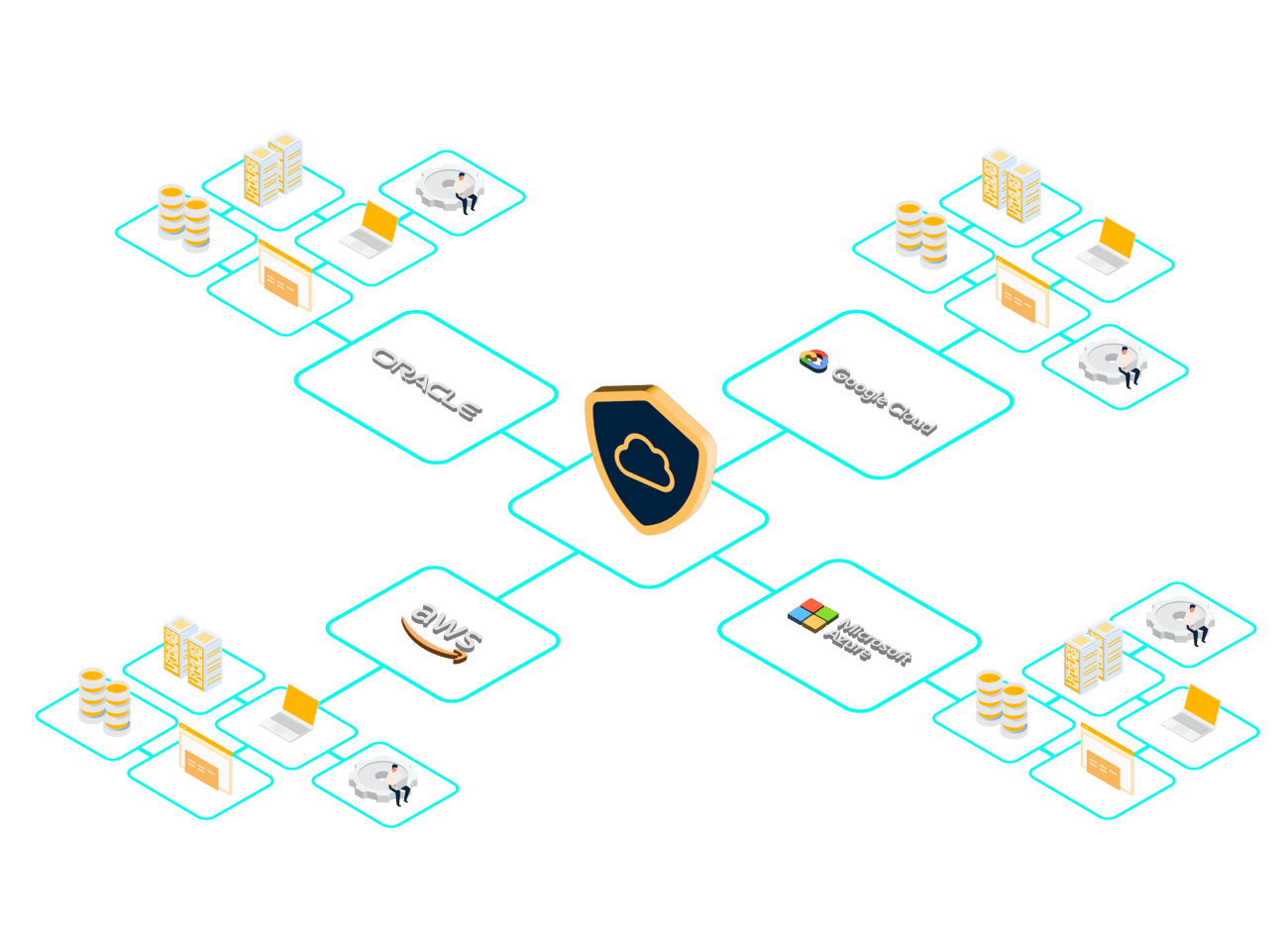
Multi-cloud platform support

Find vulnerabilities and secure cloud-native resources, such as Amazon Elastic Compute Cloud (EC2), Amazon Simple Storage Service (S3), Amazon Relational Database Service (RDS), AWS Lambda, and Amazon Virtual Private Cloud (VPC).

Safeguard resources such as Azure Virtual Machines (VMs), Azure Blob Storage, Azure SQL Database, Azure Active Directory (Azure AD), and Azure Functions.
Defend resources, such as Compute Engine, Cloud Storage, BigQuery, Kubernetes Engine (GKE), and Cloud Pub/Sub, against cybercriminals.
Shield your organization from exploitation of Oracle resources, such as Compute, Storage, Networking, Database, and Identity and Access Management (IAM).
Protect your cloud-native platforms
Comprehensive combinations with
Next-Gen Vulnerability Management
Leverage the combination of products in our unified platform.

System & Network Security
Various assessment capabilities to find vulnerabilities for all internal and internet-facing systems and servers running in your cloud-native platforms.

Web Application Security
Find vulnerabilities in your web applications running on your cloud-native platforms.

API Security
Secure your sensitive data by assessing API applications running on your cloud-native platforms.
A complete toolkit with Security Center
Discover
Automatically and continuously discover cloud-native assets.
Assess
Automatically and continuously assess cloud-native platforms to find vulnerabilities.
Prioritize
AI-driven threat intelligence to guide your vulnerability prioritization.
Remediate
Full workflow support for remediation actions.
The most powerful platform for compliance
Meet today's & future compliance requirements
Along with the growing threat landscape, new legal requirements, directives, standards, recommendations, and certifications are continuously introduced. We help you meet current and future requirements with a systematic, risk-based cyber defense, covering NIS, NIS2, DORA, CRA, GDPR, ISO 27001, and PCI DSS.

Benchmark risk against industry peers

Efficiently measure & communicate risk
We provide all the tools you need to measure and communicate risks, both internally and externally.
Benchmark your risk exposure
Gain insights into your organization's risk exposure compared to others in your industry.
All features and capabilities in
Cloud Security
How can we help you?
Your trusted partner

Frequently asked questions
Why is cloud security (CSPM) important?
As migration to cloud-native platforms exposes organizations to new and complex technologies, securing them is a big challenge. This is especially true for those organizations using not one cloud-native platform, but multiple. At the same time, business-critical operations and data are found on these platforms, making securing them critical to any organization.
What is Cloud Security Posture Management (CSPM)?
Cloud Security Posture Management (CPSM) is a vital security function for organizations operating in cloud-native platforms. It enables you to maintain a strong security posture, achieve compliance, and proactively mitigate risks.
What cloud-native platforms/vendors do you support?
We fully support the following cloud-native platforms:
- Amazon Web Services (AWS)
- Microsoft Azure
- Google Cloud
- Oracle Cloud
What cloud resources/services do you support?
We're constantly expanding our coverage of cloud resources and services. Visit our Knowledge Base to find out what we currently support.
What configurations are assessed?
Multiple security-related misconfigurations are assessed, related to:
- Network access
- Encryption
- User permissions
- Success control
- Least privilege
Is there software and/or hardware needed?
Assessments of cloud-native platforms are done using these platforms’ APIs, meaning that no additional hardware or software is required.
How soon can we get started?
Since there’s no need for software or hardware, as the implementation uses cloud-native platform APIs, you can get started within hours. Reach out and we’ll share how to get started.

