Minimize your cyber risk exposure with External Attack Surface Management
Automatically identify new internet-facing assets, monitor asset changes, eliminate blind spots, and uncover vulnerabilities.
Automated discovery, monitoring & vulnerability management - all in one
Understand your exposure & find blank spots
Our platform continuously identifies new assets, blank spots, and shadow IT.
Automatically monitor attack surface changes
Our event monitoring ensures you receive automatic notifications whenever unwanted asset changes are detected.
Minimize
the attack
surface
Gaining insight into your attack surface enables you to reduce it by eliminating unnecessary assets, shadow IT, and blind spots.
Find vulnerabilities
Automatically find vulnerabilities in assets across your attack surface.
Create a proactive cyber defense
Combining EASM with our market-leading Next-Gen Vulnerability Management Platform provides a solid foundation for a proactive cyber defense.
Watch our platform demo
Our market-leading platform is the cornerstone of a proactive cyber defense, empowering you to always stay one step ahead of cybercriminals.
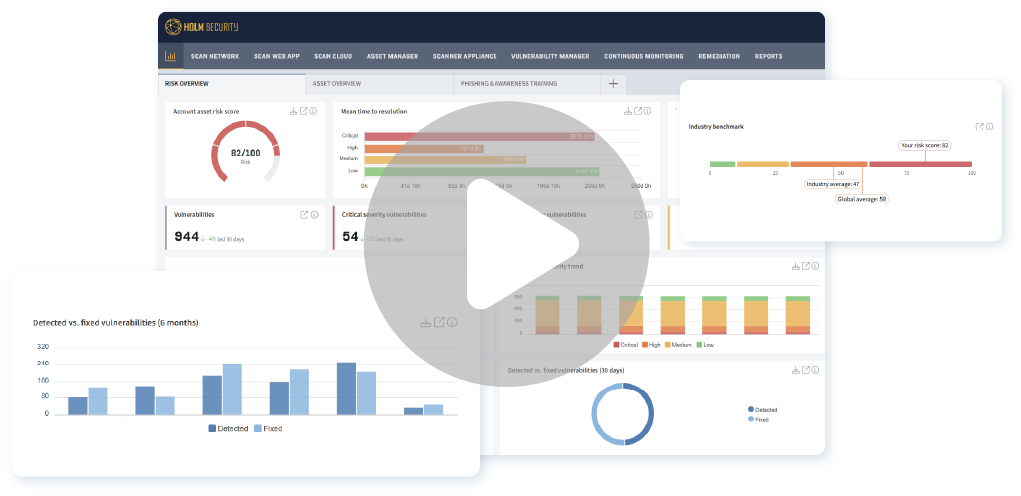
Integrated vulnerability management that’s found over 200,000 vulnerabilities
Integrating vulnerability management and External Attack Surface Management fully automates the process from asset discovery and monitoring to finding vulnerabilities.
Identify all your assets with External Attack Surface Management

Automatically discover & monitor a wide range of assets
All kinds of systems
Discover all types of systems, such as servers, virtual servers, IoT, and network equipment.
Web assets
Discover web applications running on your web servers.
API assets
Discover all APIs running on your web servers.
Domain assets
Discover sub-domains based on your domain names.
Cloud-native assets
Discover cloud assets and resources in your cloud-native platforms.
A complete workflow from discovery to remediation
Discover & monitor assets
Automatically and continuously discover changes within assets, such as new assets and changes for network assets, systems/servers, cloud-native platform assets, domain, and web assets.
Reduce attack surface
Identify unnecessary assets, blank spots, and shadow IT to reduce your exposure.
Remediate vulnerabilities
Delivering comprehensive insights to help you understand and prioritize the remediation of identified vulnerabilities.
Assess assets
Find vulnerabilities based on their severity, potential impact, ransomware exposure, and the likelihood of exploitation.
Verification
Verify the efficiency of your remediation efforts.
Benchmarking
Understand how your organizations’ risk exposure compares to other organizations in the same industry.
Reporting
Keep track of risk development with internal and external reporting based on smart key metrics.
All features and capabilities in External Attack Surface Management
How can we help you?
Your trusted partner

Frequently asked questions
What is External Attack Surface Management?
External Attack Surface Management (EASM) is the continuous process of identifying, classifying, and managing the potential entry points (attack vectors) that a cybercriminal could exploit to gain unauthorized access to a system or data.
Key components:
- Discovery
Continuously identify all assets, such as network assets, systems/servers, cloud-native platform assets, domain, and web assets, that form part of your organizations’ external attack surface.
- Inventory and classification
Create and maintain an inventory of assets and classify them based on risk and exposure.
- Risk analysis
Assess the risk associated with each asset by understanding its exposure and the potential impact of its compromise.
- Monitoring and management
Continuously monitor your attack surface for changes and emerging threats and take steps to manage and reduce risks.
Goals:
- Provide a comprehensive view of all possible attack vectors.
- Reduce your attack surface by eliminating unnecessary or vulnerable assets.
- Improve your organizations’ ability to prevent attacks by effectively understanding and managing your attack surface.
Is External Attack Surface Management a part of your platform and products?
Yes, when using any of the following products, External Attack Surface Management is included:
- System & Network Security
Discover and monitor all types of system assets, web and API assets.
- Web Application Security
Domain asset discovery and monitoring.
- Cloud Security (CSPM)
Discover and monitor cloud resource assets.
Does your External Attack Surface Management discover blank spots and shadow IT?
Yes, our platform continuously discovers assets that you may be unaware of, such as blank spots and shadow IT.
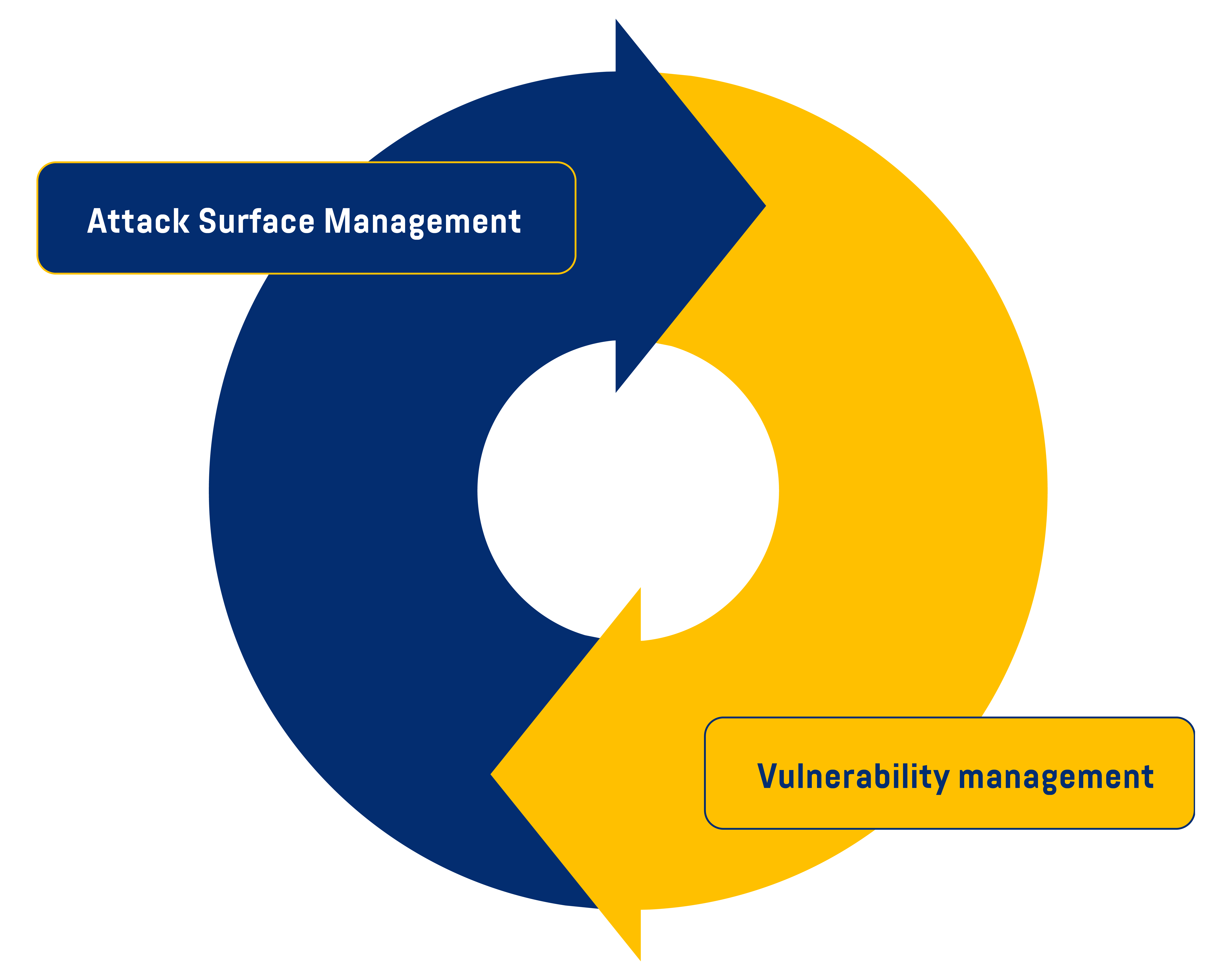
What is the difference between External Attack Surface Management and vulnerability management?
External Attack Surface Management aims to reduce your number of potential attack vectors and manage the risk associated with your attack surface. In contrast, vulnerability management aims to ensure the security of systems and applications by addressing known vulnerabilities.
What is the difference between External Attack Surface Management (EASM) and Attack Surface Management (ASM)?
ASM includes both internal and external assets, providing a holistic view of the entire IT environment, while EASM focuses exclusively on internet-facing assets.
What does your External Attack Surface Management discover?
Automatically and continuously discover new assets and asset changes within the following asset types. You can automatically assess these assets to find vulnerabilities based on the findings.
- All kinds of systems/servers
- Web applications
- API applications
- Domain assets
- Cloud-native assets
Do I need External Attack Surface Management and vulnerability management?
Yes, it's essential to both understand and reduce the attack surface, as well as understand and remediate the vulnerabilities found in your attack surface.
